Ubuntuでセキュアブートの証明書データを表示してみたが、まだ古いままで書き換わっていない。Windows Updateで自動更新されるそうだが、本当なのだろうか...。
・Windows Secure Boot certificate expiration and CA updates
・Windows セキュア ブート キーの作成と管理のガイダンス
更新前後の概要
NVRAM内に書き込まれた証明書| no. | key name | 更新前 | |
|---|---|---|---|
| 1 | Lenovo UEFI CA 2014 | 2014/01/14 ~ 2034/01/19 | |
| 2 | Trust - Lenovo Certificate | 2013/05/07 ~ 2033/05/07 | |
| 3 | Microsoft Corporation UEFI CA 2011 | 2011/06/27 ~ 2026/06/27 | |
| 4 | Microsoft Windows Production PCA 2011 | 2011/10/19 ~ 2026/10/19 |
セキュアブートが有効化されているか
セキュアブートが有効かどうか
$ sudo mokutil --sb-state SecureBoot enabled
証明書の更新前
マザーボード(NVRAM) に直接保存されている「署名データベース(db)」
$ sudo mokutil --db [key 1] SHA1 Fingerprint: cb:02:59:71:48:26:c8:67:d1:42:2c:31:0b:88:15:01:60:39:8f:0b Certificate: Data: Version: 3 (0x2) Serial Number: 03:09:48:62:90:34:75:92:87:34:95:87:23:09:4d Signature Algorithm: sha256WithRSAEncryption Issuer: C=US, ST=North Carolina, O=Lenovo, CN=Lenovo UEFI CA 2014 Validity Not Before: Jan 24 16:14:24 2014 GMT Not After : Jan 19 16:14:24 2034 GMT Subject: C=US, ST=North Carolina, O=Lenovo, CN=Lenovo UEFI CA 2014 Subject Public Key Info: Public Key Algorithm: rsaEncryption Public-Key: (2048 bit) Modulus: 00:bc:3b:83:b8:70:b0:8b:93:4a:c8:2a:af:17:c9: b1:99:1f:45:65:13:27:3c:0c:63:df:07:fd:f0:09: ~~~~~~ 省略 ~~~~~~ 40:18:8b:ba:ae:5c:25:66:ce:00:3b:10:30:ae:f0: 16:c9:86:c8:b2:20:57:11:d5:ce:a3:ac:22:71:f9: a4:e3 Exponent: 65537 (0x10001) X509v3 extensions: X509v3 Subject Key Identifier: 4B:91:A6:87:32:EA:EF:DD:2C:8F:FF:FC:6B:02:7E:C3:44:9E:9C:8F X509v3 Authority Key Identifier: 4B:81:C7:50:AC:1E:A5:1F:CB:5F:FA:18:1B:74:32:CB:2D:68:62:8E X509v3 Basic Constraints: CA:TRUE Signature Algorithm: sha256WithRSAEncryption Signature Value: 05:53:5b:d7:2e:69:e0:a0:fa:47:14:3f:e5:97:2a:75:3e:41: 18:ca:c3:51:60:67:1c:08:2c:ff:f3:86:ac:19:57:e7:77:07: ~~~~~~ 省略 ~~~~~~ cb:bd:b0:b1:b7:1a:cf:05:67:16:f8:c8:cb:f3:4a:44:ff:2c: 85:5a:9d:dc [key 2] SHA1 Fingerprint: d0:b0:89:ce:2f:5b:4d:fe:fd:a5:99:40:f7:fd:85:2b:2c:b2:a6:cb Certificate: Data: Version: 3 (0x2) Serial Number: (Negative)43:e6:33:09:7b:b9:3e:74:b5:f7:23:16:4e:34:b2:15 Signature Algorithm: sha256WithRSAEncryption Issuer: CN=Trust - Lenovo Certificate Validity Not Before: May 7 03:05:34 2013 GMT Not After : May 7 03:05:33 2033 GMT Subject: CN=Trust - Lenovo Certificate Subject Public Key Info: Public Key Algorithm: rsaEncryption Public-Key: (2048 bit) Modulus: 00:cb:61:82:5e:71:c0:f4:41:ad:f4:74:ff:b9:84: ad:76:ea:9d:6a:2e:14:02:4e:6e:b8:27:e3:2c:f1: ~~~~~~ 省略 ~~~~~~ 2e:05:6b:9b:dc:c7:33:a3:a1:b6:54:28:38:8c:64: fc:d7 Exponent: 65537 (0x10001) X509v3 extensions: 2.5.29.1: 0M..F.$v..&=H.....`".'0%1#0!..U....Trust - Lenovo Certificate.......F..J.....M. Signature Algorithm: sha256WithRSAEncryption Signature Value: 07:5e:a7:46:3b:60:f6:25:60:ad:25:96:2b:0e:d7:35:e0:b3: 28:7e:16:97:9b:e9:7d:48:5f:87:97:c7:82:cd:16:a3:8d:ed: ~~~~~~ 省略 ~~~~~~ 41:bd:f4:7e:bb:01:82:d7:c7:65:b3:8a:e3:51:8a:c5:22:30: f1:50:1f:71 [key 3] SHA1 Fingerprint: 46:de:f6:3b:5c:e6:1c:f8:ba:0d:e2:e6:63:9c:10:19:d0:ed:14:f3 Certificate: Data: Version: 3 (0x2) Serial Number: 61:08:d3:c4:00:00:00:00:00:04 Signature Algorithm: sha256WithRSAEncryption Issuer: C=US, ST=Washington, L=Redmond, O=Microsoft Corporation, CN=Microsoft Corporation Third Party Marketplace Root Validity Not Before: Jun 27 21:22:45 2011 GMT Not After : Jun 27 21:32:45 2026 GMT Subject: C=US, ST=Washington, L=Redmond, O=Microsoft Corporation, CN=Microsoft Corporation UEFI CA 2011 Subject Public Key Info: Public Key Algorithm: rsaEncryption Public-Key: (2048 bit) Modulus: 00:a5:08:6c:4c:c7:45:09:6a:4b:0c:a4:c0:87:7f: 06:75:0c:43:01:54:64:e0:16:7f:07:ed:92:7d:0b: ~~~~~~ 省略 ~~~~~~ ef:54:71:00:ce:50:35:58:76:95:08:ee:6a:b1:a2: 01:d5 Exponent: 65537 (0x10001) X509v3 extensions: 1.3.6.1.4.1.311.21.1: ..... 1.3.6.1.4.1.311.21.2: ....k..wSJ.%7.N.&{. p. X509v3 Subject Key Identifier: 13:AD:BF:43:09:BD:82:70:9C:8C:D5:4F:31:6E:D5:22:98:8A:1B:D4 1.3.6.1.4.1.311.20.2: . .S.u.b.C.A X509v3 Key Usage: Digital Signature, Certificate Sign, CRL Sign X509v3 Basic Constraints: critical CA:TRUE X509v3 Authority Key Identifier: 45:66:52:43:E1:7E:58:11:BF:D6:4E:9E:23:55:08:3B:3A:22:6A:A8 X509v3 CRL Distribution Points: Full Name: URI:http://crl.microsoft.com/pki/crl/products/MicCorThiParMarRoo_2010-10-05.crl Authority Information Access: CA Issuers - URI:http://www.microsoft.com/pki/certs/MicCorThiParMarRoo_2010-10-05.crt Signature Algorithm: sha256WithRSAEncryption Signature Value: 35:08:42:ff:30:cc:ce:f7:76:0c:ad:10:68:58:35:29:46:32: 76:27:7c:ef:12:41:27:42:1b:4a:aa:6d:81:38:48:59:13:55: ~~~~~~ 省略 ~~~~~~ 86:87:94:f6:e0:ae:02:45:ee:65:c2:b6:a3:7e:69:16:75:07: 92:9b:f5:a6:bc:59:83:58 [key 4] SHA1 Fingerprint: 58:0a:6f:4c:c4:e4:b6:69:b9:eb:dc:1b:2b:3e:08:7b:80:d0:67:8d Certificate: Data: Version: 3 (0x2) Serial Number: 61:07:76:56:00:00:00:00:00:08 Signature Algorithm: sha256WithRSAEncryption Issuer: C=US, ST=Washington, L=Redmond, O=Microsoft Corporation, CN=Microsoft Root Certificate Authority 2010 Validity Not Before: Oct 19 18:41:42 2011 GMT Not After : Oct 19 18:51:42 2026 GMT Subject: C=US, ST=Washington, L=Redmond, O=Microsoft Corporation, CN=Microsoft Windows Production PCA 2011 Subject Public Key Info: Public Key Algorithm: rsaEncryption Public-Key: (2048 bit) Modulus: 00:dd:0c:bb:a2:e4:2e:09:e3:e7:c5:f7:96:69:bc: 00:21:bd:69:33:33:ef:ad:04:cb:54:80:ee:06:83: ~~~~~~ 省略 ~~~~~~ 87:65:b4:43:18:a8:b2:e0:6d:19:77:ec:5a:24:fa: 48:03 Exponent: 65537 (0x10001) X509v3 extensions: 1.3.6.1.4.1.311.21.1: ... X509v3 Subject Key Identifier: A9:29:02:39:8E:16:C4:97:78:CD:90:F9:9E:4F:9A:E1:7C:55:AF:53 1.3.6.1.4.1.311.20.2: . .S.u.b.C.A X509v3 Key Usage: Digital Signature, Certificate Sign, CRL Sign X509v3 Basic Constraints: critical CA:TRUE X509v3 Authority Key Identifier: D5:F6:56:CB:8F:E8:A2:5C:62:68:D1:3D:94:90:5B:D7:CE:9A:18:C4 X509v3 CRL Distribution Points: Full Name: URI:http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl Authority Information Access: CA Issuers - URI:http://www.microsoft.com/pki/certs/MicRooCerAut_2010-06-23.crt Signature Algorithm: sha256WithRSAEncryption Signature Value: 14:fc:7c:71:51:a5:79:c2:6e:b2:ef:39:3e:bc:3c:52:0f:6e: 2b:3f:10:13:73:fe:a8:68:d0:48:a6:34:4d:8a:96:05:26:ee: ~~~~~~ 省略 ~~~~~~ bd:75:10:77:7d:3d:f3:45:b9:9f:97:9f:cb:57:80:6f:33:a9: 04:cf:77:a4:62:1c:59:7e
SHIMブートローダーが独自に管理している「MOKリスト」
$ sudo mokutil --list-enrolled [key 1] SHA1 Fingerprint: 76:a0:92:06:58:00:bf:37:69:01:c3:72:cd:55:a9:0e:1f:de:d2:e0 Certificate: Data: Version: 3 (0x2) Serial Number: b9:41:24:a0:18:2c:92:67 Signature Algorithm: sha256WithRSAEncryption Issuer: C=GB, ST=Isle of Man, L=Douglas, O=Canonical Ltd., CN=Canonical Ltd. Master Certificate Authority Validity Not Before: Apr 12 11:12:51 2012 GMT Not After : Apr 11 11:12:51 2042 GMT Subject: C=GB, ST=Isle of Man, L=Douglas, O=Canonical Ltd., CN=Canonical Ltd. Master Certificate Authority Subject Public Key Info: Public Key Algorithm: rsaEncryption Public-Key: (2048 bit) Modulus: 00:bf:5b:3a:16:74:ee:21:5d:ae:61:ed:9d:56:ac: bd:de:de:72:f3:dd:7e:2d:4c:62:0f:ac:c0:6d:48: ~~~~~~ 省略 ~~~~~~ 32:d1:a0:1c:57:a8:4d:e3:af:a5:8e:05:05:3e:10: 43:a1 Exponent: 65537 (0x10001) X509v3 extensions: X509v3 Subject Key Identifier: AD:91:99:0B:C2:2A:B1:F5:17:04:8C:23:B6:65:5A:26:8E:34:5A:63 X509v3 Authority Key Identifier: AD:91:99:0B:C2:2A:B1:F5:17:04:8C:23:B6:65:5A:26:8E:34:5A:63 X509v3 Basic Constraints: critical CA:TRUE X509v3 Key Usage: Digital Signature, Certificate Sign, CRL Sign X509v3 CRL Distribution Points: Full Name: URI:http://www.canonical.com/secure-boot-master-ca.crl Signature Algorithm: sha256WithRSAEncryption Signature Value: 3f:7d:f6:76:a5:b3:83:b4:2b:7a:d0:6d:52:1a:03:83:c4:12: a7:50:9c:47:92:cc:c0:94:77:82:d2:ae:57:b3:99:04:f5:32: ~~~~~~ 省略 ~~~~~~ 14:db:ce:03:0e:0b:66:c4:1c:6d:bd:b8:27:77:c1:42:94:bd: fc:6a:0a:bc [key 2] SHA1 Fingerprint: a8:60:2c:93:b5:13:95:e4:95:33:53:0a:ae:26:64:f5:eb:b3:74:b6 Certificate: Data: Version: 3 (0x2) Serial Number: 4d:9b:cd:13:28:10:11:d8:78:b1:7e:eb:f2:c5:0d:ca:38:b3:63:1e Signature Algorithm: sha256WithRSAEncryption Issuer: CN=VMware Validity Not Before: Dec 16 13:31:18 2021 GMT Not After : Nov 22 13:31:18 2121 GMT Subject: CN=VMware Subject Public Key Info: Public Key Algorithm: rsaEncryption Public-Key: (2048 bit) Modulus: 00:cc:ea:1e:0c:41:c4:e1:b0:03:4a:76:96:c8:a7: 20:9c:ab:1a:14:69:27:84:e8:1d:2a:17:33:c3:97: ~~~~~~ 省略 ~~~~~~ 13:7c:29:8c:81:f2:c5:c6:a1:dc:09:03:65:1a:29: 97:fd Exponent: 65537 (0x10001) X509v3 extensions: X509v3 Subject Key Identifier: 31:36:87:94:ED:7A:CA:55:5F:23:CB:D4:F7:CD:C4:E1:28:DE:B5:F6 X509v3 Authority Key Identifier: 31:36:87:94:ED:7A:CA:55:5F:23:CB:D4:F7:CD:C4:E1:28:DE:B5:F6 X509v3 Basic Constraints: critical CA:TRUE Signature Algorithm: sha256WithRSAEncryption Signature Value: a2:96:88:05:25:5e:0e:6a:38:72:9c:b5:70:50:e7:69:c2:73: 96:3d:d1:44:5d:81:dd:13:6a:55:44:50:48:7a:0e:9c:47:18: ~~~~~~ 省略 ~~~~~~ 62:70:0d:33:22:ed:45:f4:bb:2e:eb:d2:16:8f:49:87:20:22: d7:19:94:07
PCのファームウエアを手動でアップデート
Lenovo M720q の最新ファームウエアを公式Webからダウンロードする
付属ドキュメントm1ujy78usa.txtより、重要箇所の抜粋
Flash BIOS update - Flash from Operating System version
for ThinkCentre M720t, M720s, M720q, M920t, M920s, M920q, M920x, ThinkStation P330 Tiny
Version M1UKT78A
Installation README
Installing the package
======================
5. You may first see a confirmation prompt "Proceed with BIOS
update now?". Click "Yes" to continue.
6. You will see the prompt "Would you like to update the Serial
Number?". Input "n" and press Enter.
7. Then you will see the prompt "Would you like to update the
Machine Type and Model?". Input "n" and press Enter again.
Then the BIOS update process will start.
8. The update may take up to 2 minutes. Do not power off or restart
the system during this procedure! After the Windows update
process ends, the system will automatically reboot to continue
the flash process.
Summary of Changes
==================
CHANGES for M1UKT78A / WU Version 1.0.0.120
- Update Microsoft UEFI CA 2023 and Option ROM UEFI CA 2023.
- Add Microsoft Corporation KEK 2K CA 2023 and Windows UEFI CA 2023.
Windows上でアップデートパッケージ(m1ujy78usa.exe)を実行し、付属ドキュメント(m1ujy78usa.txt)の質問事項6.と7.を選択するダイアログを確認した後に、書き込み開始。
再起動を促すダイアログが出るので、再起動すると次のBIOS画面が表示されアップデートが始まる。
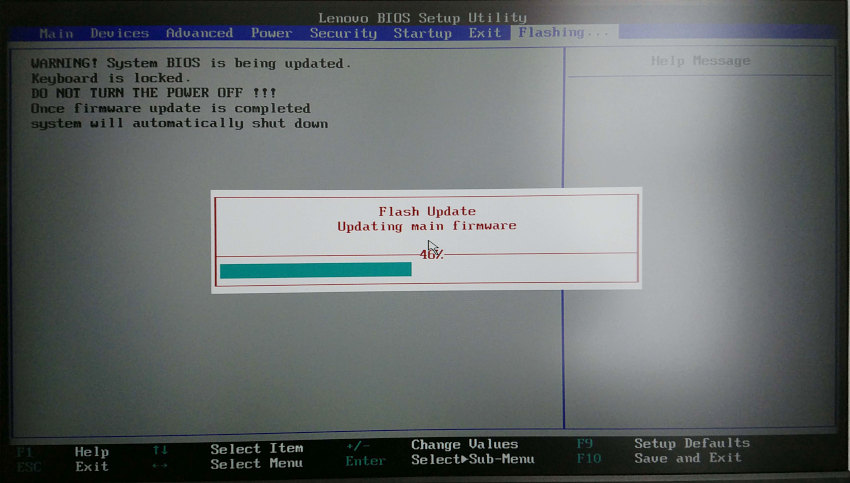
BIOS Firmwareアップデート中の画面 (100% まで2分ほど掛かる)
その後自動的に再起動がかかり、通常利用できるようになる。
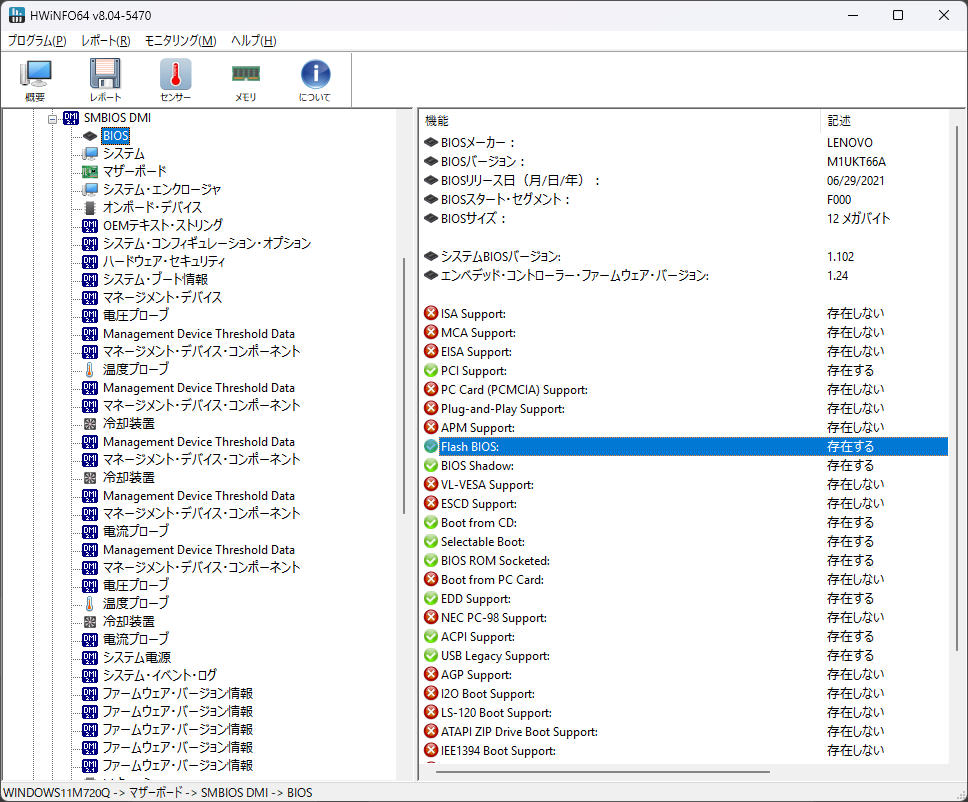
WindowsでHWiNFOを実行し、BIOSバージョンを確認 (更新前)
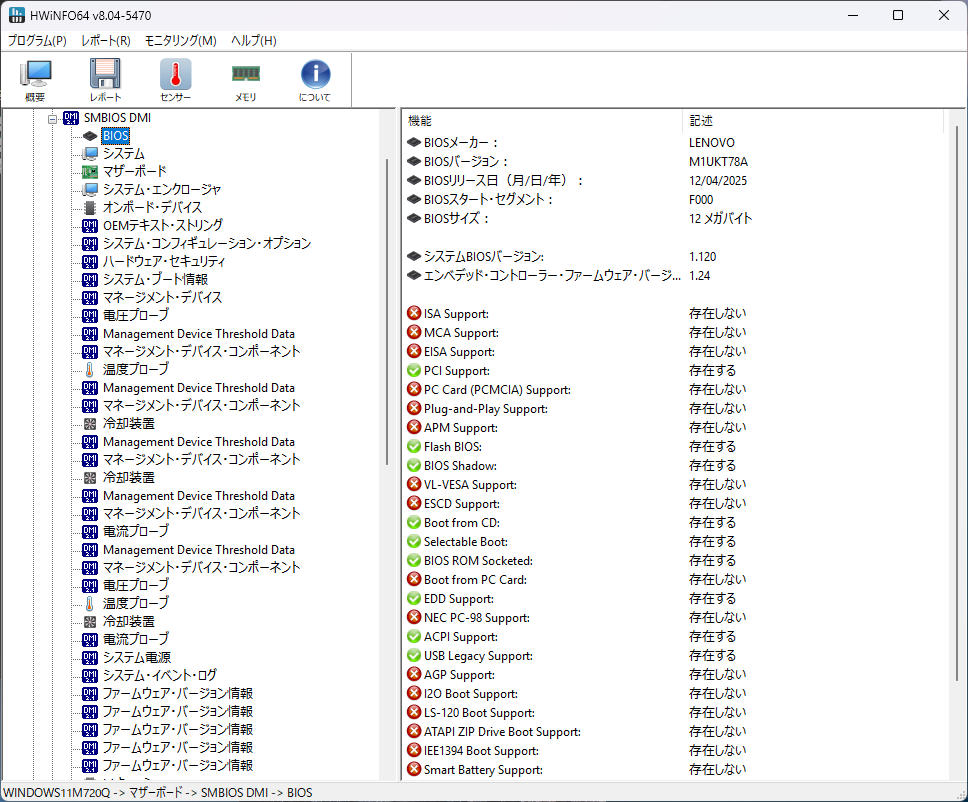
WindowsでHWiNFOを実行し、BIOSバージョンを確認 (更新後)
BIOSのバージョンが確かに上がっていることを確認後、Ubuntuのmokutil --dbで証明書を確認するが、ここはBIOS更新前と完全に同一だった。
付属ドキュメントには " CHANGES for M1UKT78A / WU Version 1.0.0.120 " のように書かれているので、Windows Updateを確認してみると、オプションの更新セクションに1つ前のバージョン 1.0.0.119 が表示されている。
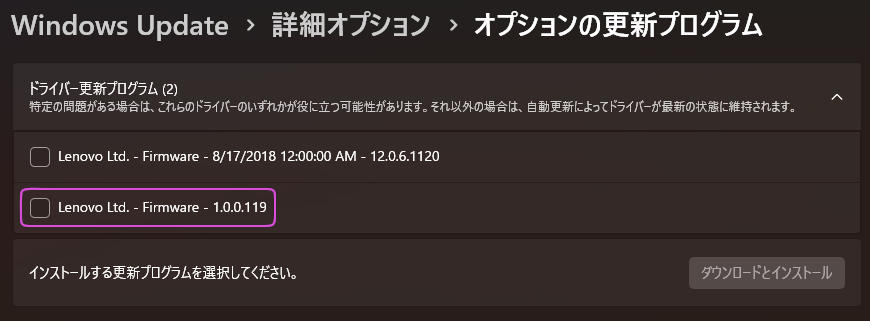
Windows Updateのファームウエア更新(オプションの更新)
残念ながら、この機種向けのファームウエア最新版はMicrosoft側からは配布されていない模様だ。